What
is registry ?
Database of stored configuration information about the users, hardware, and software on a Windows system.
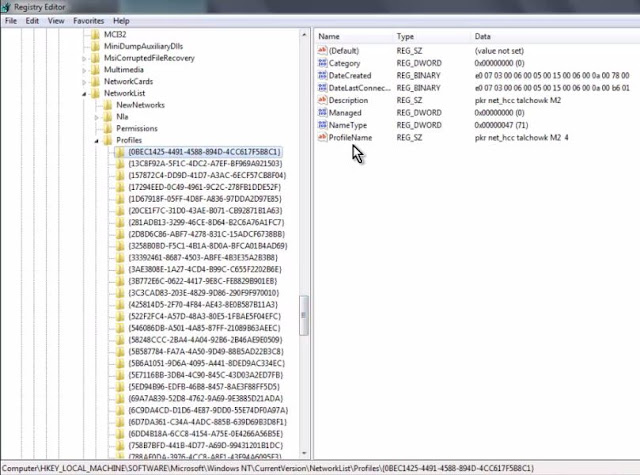
CurrentVersion\NetworkList\Profiles
Below you can see my lab setup image.
In right hand side, you're seeing "ProfileName" as pkr net_hcc talchowkm2 4.
Now, we can say, indeed the system was connected to AP.
Information that can be found in the registry includes:
Users and the time they last used the system
Most recently used software
Any devices mounted to the system including unique identifiers of flash drives, hard drives, phones, tablets, etc.
When the system connected to a specific wireless access point
What and when files were accessed
A list any searches done on the system
And much, much more
Video Tutorial of this part is in youtube HERE
*My resource for this tutorial :
Database of stored configuration information about the users, hardware, and software on a Windows system.
Although the registry was designed to configure the system, to do so, it tracks such a huge information about the user's activities, the devices connected to system, what software was used & when etc. All of this can be useful for the forensic investigator in tracking the who, what, where, & when of a forensic investigation. The key is just knowing where to look for it.
In this article :
As a forensic analyst, the registry can be a best place for evidence of what, where, when, and how something occurred on the system.
In this step by step tutorial, we will see how the Windows registry works and what evidence it leaves behind when someone uses the system for good or bad purpose. And our article will cover "Wireless Evidence"
HIVES :
Inside the registry, there are root folders. These root folders are referred to as hives. There are five (5) registry hives.
HKEY_USERS: contains all the loaded user profiles
HKEYCURRENT_USER: profile of the currently logged-on user
HKEYCLASSES_ROOT: configuration information on the application used to open files
HKEYCURRENT_CONFIG: hardware profile of the system at startup
HKEYLOCAL_MACHINE: configuration information including hardware and software settings.
HKEYCURRENT_USER: profile of the currently logged-on user
HKEYCLASSES_ROOT: configuration information on the application used to open files
HKEYCURRENT_CONFIG: hardware profile of the system at startup
HKEYLOCAL_MACHINE: configuration information including hardware and software settings.
Steps :
Getting into registry,
- Goto search, and search as "regedit.exe" (exclude quotes)
- Enter, or Click it. Then you will get following screen.
As I already mentioned above, we will see Wireless Evidence History available in registry.
Wireless Evidence in the Registry :
Forensic
investigator goes to following location in registry editor for this purpose.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows
NT\
CurrentVersion\NetworkList\Profiles
Below you can see my lab setup image.
Now, we can say, indeed the system was connected to AP.
Information that can be found in the registry includes:
Users and the time they last used the system
Most recently used software
Any devices mounted to the system including unique identifiers of flash drives, hard drives, phones, tablets, etc.
When the system connected to a specific wireless access point
What and when files were accessed
A list any searches done on the system
And much, much more
Video Tutorial of this part is in youtube HERE
*My resource for this tutorial :
-OTW
(Null-Byte)
-Nest.unm.edu
-Cybrary.it
THANK YOU FOR READING. :)


Comments
Post a Comment